Interested in working with us?
Let's chat!
Interested in working with us?
Let's chat!
The next generation
of data security
of data security
Extraordinary protection
We partner with clients from a variety of industries and backgrounds to assess present and future threats, and develop comprehensive security systems built to stand the test of time.
The next generation
of data security
of data security
Extraordinary protection
We partner with clients from a variety of industries and backgrounds to assess present and future threats, and develop comprehensive security systems built to stand the test of time.

The next generation
of data security
of data security
We play the long game. Our role is to build solutions which ensure critical data remains intergenerationally secure from threats in both the immediate and distant future.

For Big Data and Cloud Computing
Going beyond platforms
Exatect builds data foundations that outlive platforms and providers, embedding adaptive cryptography, architectural resilience, and long-term data sovereignty so information remains trusted, portable, and secure across generations of compute and threat evolution.

For Telecommunications Networks
Trust without expiration
Exatect protects the continuity of communications by designing security that survives shifting standards and network generations, ensuring identity, signaling, and data remain confidential, reliable, and trustworthy far into the future.

For Supply Chain Management
Weathering the storm
Securing the data that feeds, equips, and powers the world by hardening systems for decades of operation, preserving integrity, authenticity, and operational trust across aging assets, modern upgrades, and an ever-changing risk landscape.

For Big Data and Cloud Computing
Going beyond platforms
Exatect builds data foundations that outlive platforms and providers, embedding adaptive cryptography, architectural resilience, and long-term data sovereignty so information remains trusted, portable, and secure across generations of compute and threat evolution.

For Telecommunications Networks
Trust without expiration
Exatect protects the continuity of communications by designing security that survives shifting standards and network generations, ensuring identity, signaling, and data remain confidential, reliable, and trustworthy far into the future.

For Supply Chain Management
Weathering the storm
Securing the data that feeds, equips, and powers the world by hardening systems for decades of operation, preserving integrity, authenticity, and operational trust across aging assets, modern upgrades, and an ever-changing risk landscape.
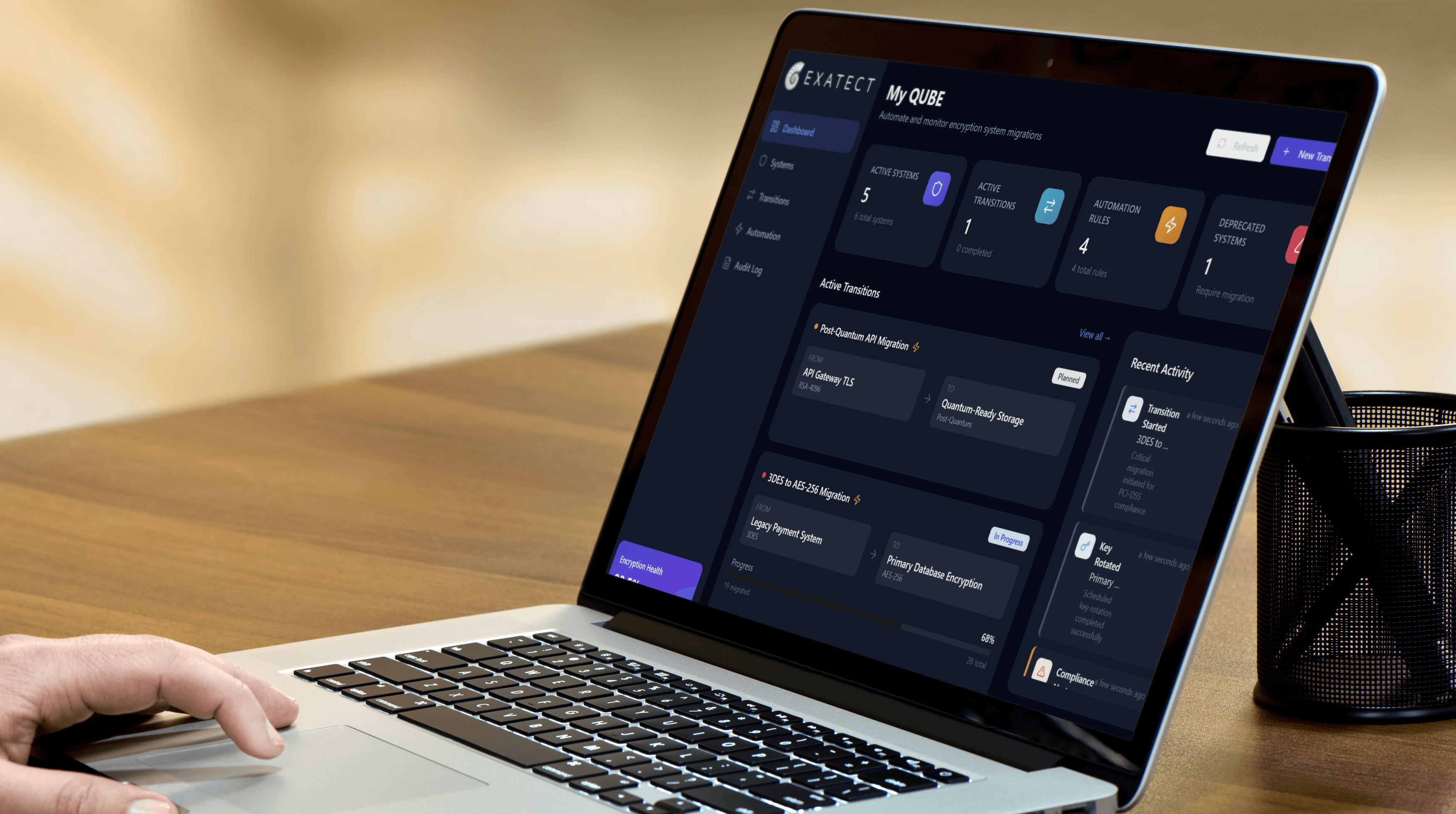
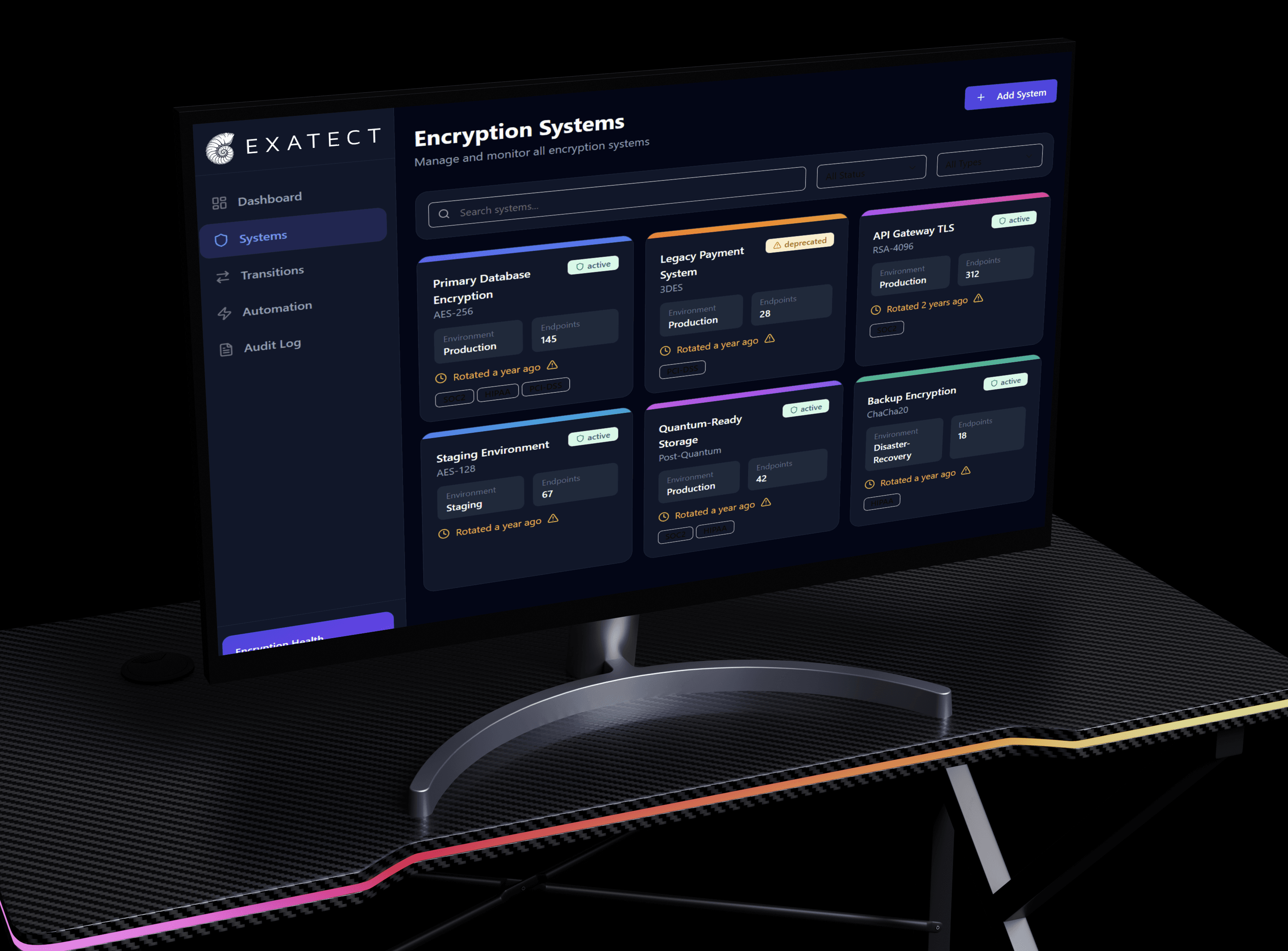
ExaQUBE
Post-quantum cryptography

Post-quantum cryptography

Post-quantum cryptography
Automated recon & reporting

Automated recon & reporting

Automated recon & reporting
One platform to seamlessly eliminate cryptographic debt
We are currently building ExaQUBE, an end-to-end platform designed to make it as easy as possible to discover cryptographic vulnerabilities and integrate new encryption protocols into large-scale systems.








our mission
our mission
our mission
Mitigating future threats
Security is built on foresight, not reaction. By identifying emerging risks before they take shape, defenses are engineered to neutralize future threats at their source. The result is protection that stays ahead of adversaries, preventing tomorrow’s risks from ever becoming today’s reality.
Continuously analyze technological, geopolitical, and adversarial trends to identify future attack vectors before they emerge.
Continuously analyze technological, geopolitical, and adversarial trends to identify future attack vectors before they emerge.
Continuously analyze technological, geopolitical, and adversarial trends to identify future attack vectors before they emerge.
Design systems with cryptographic agility and modular controls that can evolve as threats and technologies change.
Design systems with cryptographic agility and modular controls that can evolve as threats and technologies change.
Design systems with cryptographic agility and modular controls that can evolve as threats and technologies change.
Address weaknesses at the design stage, removing entire classes of future vulnerabilities before they can be exploited.
Address weaknesses at the design stage, removing entire classes of future vulnerabilities before they can be exploited.
Address weaknesses at the design stage, removing entire classes of future vulnerabilities before they can be exploited.

Modernize Encryption at Scale with Zero Disruption
New attack vectors will emerge with future trends. Our evolution must precede theirs.
Y2Q & SNDL
As quantum computing advances, current encryption and key systems will become vulnerable, requiring proactive migration to quantum-resistant cryptography and future-proof key management.
Combatting AI-Native Threats
AI will enable faster, more adaptive attacks, from automated social engineering to self-optimizing malware, demanding defenses that can anticipate and outpace intelligent adversaries.
Navigating Decentralization
Distributed architectures and decentralized platforms expand attack surfaces and introduce new trust challenges, requiring security models built for fragmented, permissionless ecosystems.
Emergent complexity risks
As systems become more interconnected and layered, hidden dependencies and cascading failures create new vulnerabilities, making resilience and visibility essential.
Democratization of Tech
Wider access to advanced tools empowers more potential attackers, increasing the volume and sophistication of threats and forcing security to scale alongside global technical literacy.
Cyber-physical convergence
As digital systems directly control physical infrastructure, attacks can move from data theft to real-world harm, demanding integrated security across both cyber and physical domains.
New attack vectors will emerge with future trends. Our evolution must precede theirs.
Y2Q & SNDL
As quantum computing advances, current encryption and key systems will become vulnerable, requiring proactive migration to quantum-resistant cryptography and future-proof key management.
Combatting AI-Native Threats
AI will enable faster, more adaptive attacks, from automated social engineering to self-optimizing malware, demanding defenses that can anticipate and outpace intelligent adversaries.
Navigating Decentralization
Distributed architectures and decentralized platforms expand attack surfaces and introduce new trust challenges, requiring security models built for fragmented, permissionless ecosystems.
Emergent complexity risks
As systems become more interconnected and layered, hidden dependencies and cascading failures create new vulnerabilities, making resilience and visibility essential.
Democratization of Tech
Wider access to advanced tools empowers more potential attackers, increasing the volume and sophistication of threats and forcing security to scale alongside global technical literacy.
Cyber-physical convergence
As digital systems directly control physical infrastructure, attacks can move from data theft to real-world harm, demanding integrated security across both cyber and physical domains.
New attack vectors will emerge with future trends. Our evolution must precede theirs.
Y2Q & SNDL
As quantum computing advances, current encryption and key systems will become vulnerable, requiring proactive migration to quantum-resistant cryptography and future-proof key management.
Combatting AI-Native Threats
AI will enable faster, more adaptive attacks, from automated social engineering to self-optimizing malware, demanding defenses that can anticipate and outpace intelligent adversaries.
Navigating Decentralization
Distributed architectures and decentralized platforms expand attack surfaces and introduce new trust challenges, requiring security models built for fragmented, permissionless ecosystems.
Emergent complexity risks
As systems become more interconnected and layered, hidden dependencies and cascading failures create new vulnerabilities, making resilience and visibility essential.
Democratization of Tech
Wider access to advanced tools empowers more potential attackers, increasing the volume and sophistication of threats and forcing security to scale alongside global technical literacy.
Cyber-physical convergence
As digital systems directly control physical infrastructure, attacks can move from data theft to real-world harm, demanding integrated security across both cyber and physical domains.
Unordinary threats demand extraordinary protection. We provide value at every step of our partnership.


0%
Downtime on systems transitioning


24/7
Support across all services

97
Threat vectors accounted for in panels


0%
Downtime on systems transitioning


24/7
Support across all services


97
Threat vectors accounted for in panels


0%
Downtime on systems transitioning


24/7
Support across all services


97
Threat vectors accounted for in panels
01
Comprehensive assessments
We evaluate your environment, identify vulnerabilities, and map critical risks to create a clear, actionable security baseline.
01
Comprehensive assessments
We evaluate your environment, identify vulnerabilities, and map critical risks to create a clear, actionable security baseline.
01
Comprehensive assessments
We evaluate your environment, identify vulnerabilities, and map critical risks to create a clear, actionable security baseline.
02
Tailored solutions & protocols
We design and implement security strategies that are specifically built for your unique needs, operational realities, and future objectives.
02
Tailored solutions & protocols
We design and implement security strategies that are specifically built for your unique needs, operational realities, and future objectives.
02
Tailored solutions & protocols
We design and implement security strategies that are specifically built for your unique needs, operational realities, and future objectives.
03
Vigilance, support, and adaptation
We stay engaged through continuous monitoring, proactive updates, and ongoing improvements to keep defenses ahead of emerging threats.
03
Vigilance, support, and adaptation
We stay engaged through continuous monitoring, proactive updates, and ongoing improvements to keep defenses ahead of emerging threats.
03
Vigilance, support, and adaptation
We stay engaged through continuous monitoring, proactive updates, and ongoing improvements to keep defenses ahead of emerging threats.
Our Journal

Supply Chain Management and Logistics in the Crosshairs of Cybersecurity Threats
Insight
1/22/26

Cybersecurity Challenges in the Telecom World: Protecting Networks in a Distributed, Data-Driven Era
Insight
11/5/25

Big Data, Cloud Computing, and the Quantum Threat
Insight
1/21/26
Explore more news and insight
Our Journal

Supply Chain Management and Logistics in the Crosshairs of Cybersecurity Threats
Insight
1/22/26

Cybersecurity Challenges in the Telecom World: Protecting Networks in a Distributed, Data-Driven Era
Insight
11/5/25

Big Data, Cloud Computing, and the Quantum Threat
Insight
1/21/26
Explore more news and insight
Our Journal

Supply Chain Management and Logistics in the Crosshairs of Cybersecurity Threats
Insight
1/22/26

Cybersecurity Challenges in the Telecom World: Protecting Networks in a Distributed, Data-Driven Era
Insight
11/5/25

Big Data, Cloud Computing, and the Quantum Threat
Insight
1/21/26
Explore more news and insight